How a 2-Hour Hack Exposed 99% of the Cloud: 3 Real-World Threats Redefining Risk in 2025
The Cloud Paradox
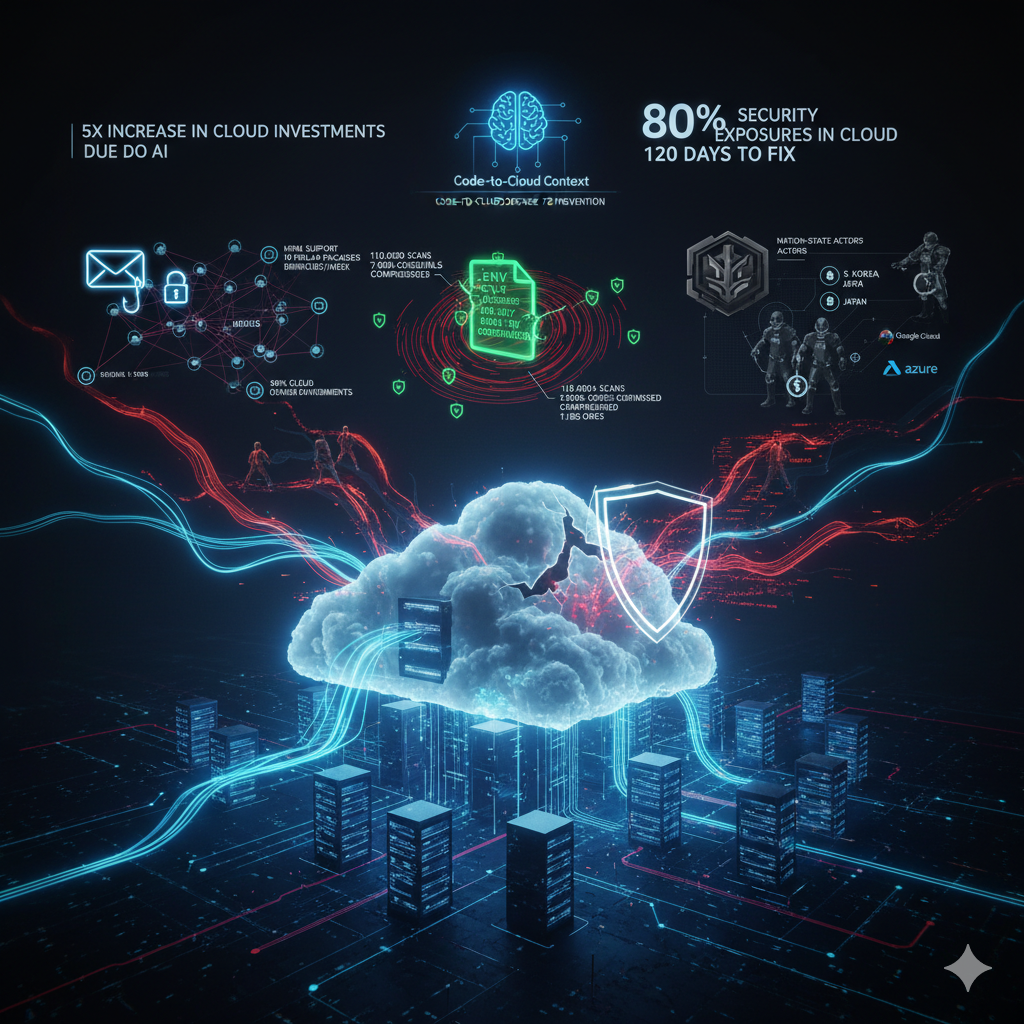
Moving to the cloud and adopting AI isn't just a trend; it's a modern business necessity, with reports showing a 5x increase in cloud investments due to AI alone. Companies are migrating operations at an unprecedented scale to innovate faster and gain a competitive edge. But there's a paradox at the heart of this transformation: as businesses have moved to the cloud, "adversaries have followed."
The scale of the challenge is staggering. Today, a full 80% of security exposures occur in the cloud, and once an issue is found, it takes an average of 120 days to fix. In this complex and fast-moving environment, it's easy to get lost in the noise of endless alerts and vulnerabilities.
This article cuts through that noise to highlight three of the most surprising and impactful findings from the current threat landscape. These stories aren't just statistics; they are critical lessons in how adversaries operate today and where our biggest risks truly lie.
1. A Single Phishing Email Compromised 99% of the Cloud
On September 8th, 2025, the software development world was shaken by a supply chain attack that demonstrated just how fragile our interconnected systems are. The attack began not with a sophisticated zero-day exploit, but with a simple, effective phishing email impersonating NPM Support. The target was a well-known open-source developer, whose stolen credentials gave the attacker the keys to the world's largest software registry for open-source JavaScript packages. The compromise became public in real-time as the developer discussed the unfolding attack on social media.
With those credentials, the attacker updated 18 popular packages—which together account for 2.6 billion downloads per week—with malicious code. These poisoned updates were live in the registry for only two hours. The injected code's goal was brutally simple: target and steal from cryptocurrency wallets.
The true significance of this attack lies in its incredible reach. It revealed that a single point of failure in the open-source ecosystem could have near-universal consequences for the entire cloud infrastructure that depends on it.
99% of cloud environments had at least one instance of one of the packages targeted by this threat actor, with the 'debug' package being the most prevalent by far.
2. One Common Mistake Exposed Over 7,000 Company Credentials
While supply chain attacks are sophisticated, some of the most devastating breaches come from a single, common oversight. A recent massive, cloud-based ransom campaign targeted one such mistake: publicly exposed .env files.
For those unfamiliar, .env files are simple text files used by developers to store sensitive configuration variables and authorization data, like API keys and database credentials, exposing credentials for services ranging from Mailgun and HubSpot to GitHub. They are the digital keys to the kingdom, and they should never be accessible from the internet.
Yet, a campaign scanning for this one vulnerability had a staggering impact:
- 110,000+ targeted domains were scanned
- 90,000+ unique sensitive variables were discovered
- 7,000+ IAM credentials were compromised across 1,185 organizations
- 1,200 cloud platform accounts were directly impacted
This incident is a powerful reminder that in the cloud, a seemingly small development oversight doesn't just create a small risk—it creates a catastrophic security failure at an enormous scale. It provides a direct and actionable lesson for every team building and deploying applications in the cloud.
3. For Some Nation-States, Hacking Isn't Just Espionage—It's GDP
When we think of cybercrime, we often picture ransomware gangs or individual hackers. But one of the three key cloud aggressors operating today is a far more formidable opponent: the nation-state. This threat is driven by sophisticated state-sponsored groups like the Lazarus Group (Alluring Pisces) and Kimsuky (Sparkling Pisces) operating out of the DPRK (North Korea).
For the DPRK, cyber operations go far beyond traditional espionage or political disruption. Their focus is on major economic gain, with a heavy emphasis on stealing cryptocurrencies. Their primary targets are organizations in South Korea, Japan, and the United States.
What's most shocking is the scale and integration of these activities into their national strategy. These crypto-focused cyberattacks are estimated to account for a massive 40% of their GDP.
This reframes the entire nature of the threat. We are not just defending against criminals seeking a payday; we are defending against highly sophisticated, state-sponsored actors pursuing a national economic strategy. These groups bring immense resources, patience, and a multi-stage approach that simple criminal campaigns lack, targeting everything from the software supply chain to the core SaaS infrastructure providers like Google Cloud and Azure. For organizations in finance and other critical sectors, this fundamentally raises the stakes.
Beyond the Frightening Facts
The stories of a fragile software supply chain, the outsized consequences of simple mistakes, and the reality of state-funded adversaries can seem overwhelming. They paint a picture of a threat landscape where defenders are constantly on the back foot.
However, the path forward isn't just about reacting faster to an infinite stream of alerts. The solution lies in achieving what security experts call "Code-to-Cloud Context." This means adopting a more integrated and intelligent approach to security—one that connects the dots all the way from the first line of code to the cloud infrastructure it runs on. By understanding the full context of how these attacks unfold, we can move from defense to prevention.
Looking at your own systems, what's the one simple oversight that could have the most surprising and widespread impact?